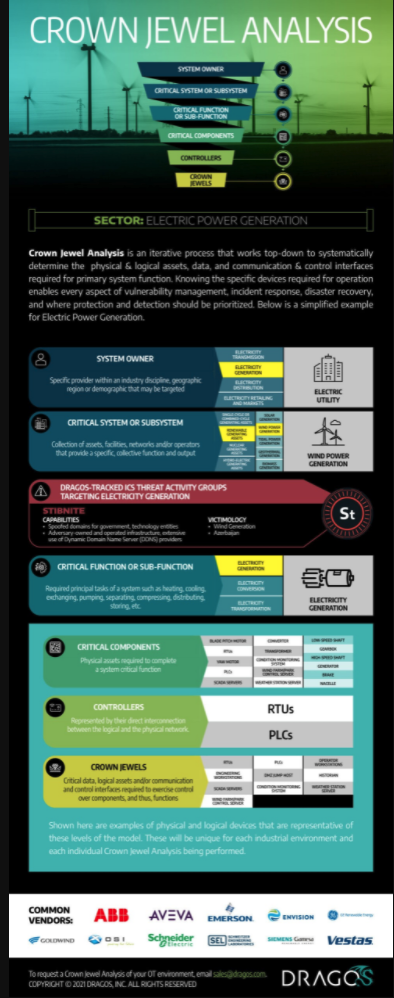
Crown Jewel Analysis is an iterative process that works top-down to systematically determine the physical & logical assets, data, and communication & control interfaces required for primary system function. Knowing the specific devices required for operation enables every aspect of vulnerability management, incident response, disaster recovery, and where protection and detection should be prioritized. Below is a simplified example for Renewable Electric Power Generation. If you’re interested in learning more, we also published a blog and an in-depth whitepaper on this important topic.
